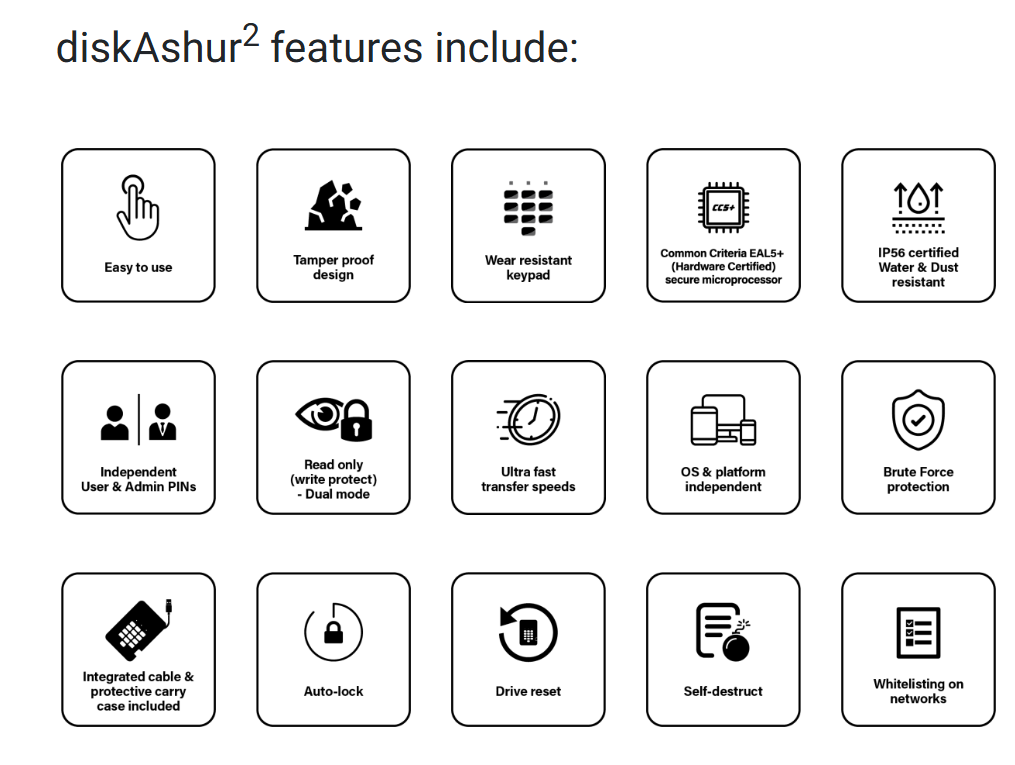
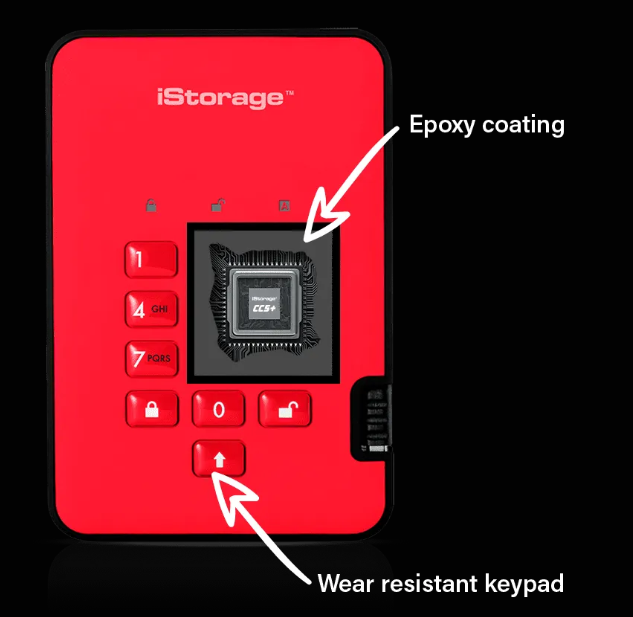
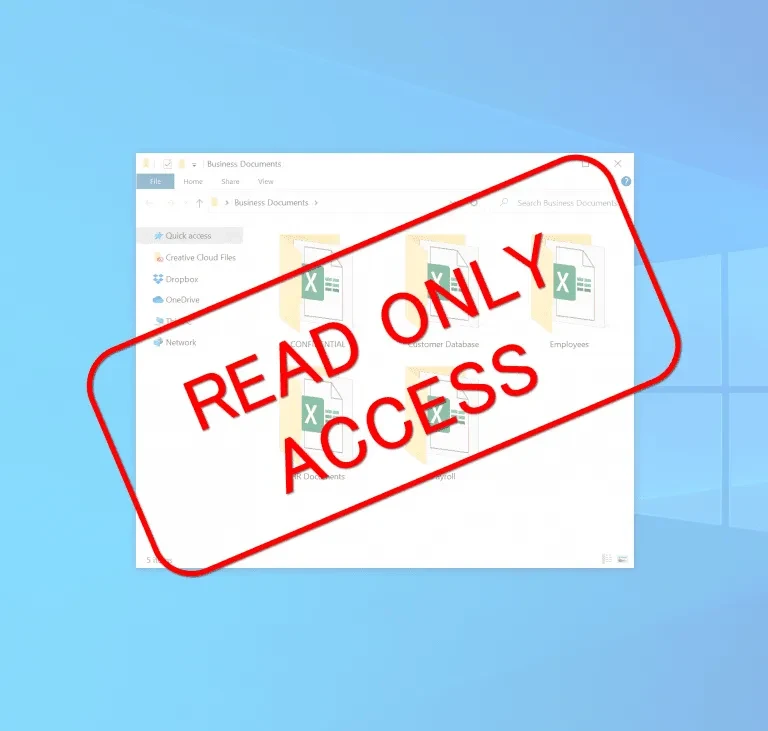
-
×
 זיכרון נייד מוצפן (דיסק און קי) - Apricorn | ASK3-NXC-128GB | Aegis Secure Key | 3NXC | 128GB | USB 3.2 Type-C Encrypted Flash Key
3 × ₪ 0
זיכרון נייד מוצפן (דיסק און קי) - Apricorn | ASK3-NXC-128GB | Aegis Secure Key | 3NXC | 128GB | USB 3.2 Type-C Encrypted Flash Key
3 × ₪ 0 -
×
 כונן קשיח חיצוני מוגן כתיבה - Kanguru | U3-2HDWP-4T | UltraLock | 4TB HDD | USB 3.0 | Write Protected
1 × ₪ 0
כונן קשיח חיצוני מוגן כתיבה - Kanguru | U3-2HDWP-4T | UltraLock | 4TB HDD | USB 3.0 | Write Protected
1 × ₪ 0 -
×
 דיסק קשיח חיצוני חומרה מוצפנת - Apricorn | AFL3-2TB | Aegis Fortress L3 | 2TB HDD USB3.0 Hardware Encrypted
1 × ₪ 0
דיסק קשיח חיצוני חומרה מוצפנת - Apricorn | AFL3-2TB | Aegis Fortress L3 | 2TB HDD USB3.0 Hardware Encrypted
1 × ₪ 0 -
×
 זיכרון נייד מוגן כתיבה מהירות גבוהה (דיסק און קי) - Kanguru KF3WP-512GB | SS3 | 512GB | USB 3.0 Write Protected
1 × ₪ 0
זיכרון נייד מוגן כתיבה מהירות גבוהה (דיסק און קי) - Kanguru KF3WP-512GB | SS3 | 512GB | USB 3.0 Write Protected
1 × ₪ 0 -
×
 כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-2T | UltraLock | 2TB USB-C | M.2 NVMe | Write Protected
3 × ₪ 0
כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-2T | UltraLock | 2TB USB-C | M.2 NVMe | Write Protected
3 × ₪ 0 -
×
 זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDF3000-64G | Defender 3000 | 64GB | USB 3.0 | FIPS 140-2 Level 3
1 × ₪ 0
זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDF3000-64G | Defender 3000 | 64GB | USB 3.0 | FIPS 140-2 Level 3
1 × ₪ 0 -
×
 דיסק קשיח חיצוני חומרה מוצפנת - Apricorn | AFL3-1TB | Aegis Fortress L3 | 1TB HDD USB3.0 Hardware Encrypted
3 × ₪ 0
דיסק קשיח חיצוני חומרה מוצפנת - Apricorn | AFL3-1TB | Aegis Fortress L3 | 1TB HDD USB3.0 Hardware Encrypted
3 × ₪ 0 -
×
 כונן חיצוני SSD מוצפן - Apricorn | ASSD-3PL256-480F | Aegis Padlock SSD | 480GB | USB3.0 | AES 256-Bit Hardware Encryption
6 × ₪ 0
כונן חיצוני SSD מוצפן - Apricorn | ASSD-3PL256-480F | Aegis Padlock SSD | 480GB | USB3.0 | AES 256-Bit Hardware Encryption
6 × ₪ 0 -
×
 כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-500G | UltraLock | 500GB USB-C | M.2 NVMe | Write Protected
1 × ₪ 0
כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-500G | UltraLock | 500GB USB-C | M.2 NVMe | Write Protected
1 × ₪ 0 -
×
 זיכרון נייד מוצפן (דיסק און קי) -Apricorn | ASK3-NXC-32GB | Aegis Secure Key | 3NXC | 32GB | USB3.2 Type-C Encrypted Flash Key
4 × ₪ 0
זיכרון נייד מוצפן (דיסק און קי) -Apricorn | ASK3-NXC-32GB | Aegis Secure Key | 3NXC | 32GB | USB3.2 Type-C Encrypted Flash Key
4 × ₪ 0 -
×
 זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDF3000-256G | Defender 3000 | 256GB | USB 3.0 | FIPS 140-2 Level 3
1 × ₪ 0
זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDF3000-256G | Defender 3000 | 256GB | USB 3.0 | FIPS 140-2 Level 3
1 × ₪ 0 -
×
 זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDFE30-16GB | Defender Elite 30 | 16GB | USB 3.0 | AES 256-Bit Hardware Encryption
4 × ₪ 0
זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDFE30-16GB | Defender Elite 30 | 16GB | USB 3.0 | AES 256-Bit Hardware Encryption
4 × ₪ 0 -
×
 כונן חיצוני SSD מוצפן - Apricorn | ASSD-3PL256-240F | Aegis Padlock SSD | 240GB | USB3.0 | AES 256-Bit Hardware Encryption
1 × ₪ 0
כונן חיצוני SSD מוצפן - Apricorn | ASSD-3PL256-240F | Aegis Padlock SSD | 240GB | USB3.0 | AES 256-Bit Hardware Encryption
1 × ₪ 0 -
×
 זיכרון נייד מוצפן (דיסק און קי) -Apricorn | ASK3-240GB | 240GB | Aegis Secure Key | USB3.1 Encrypted Flash Key
1 × ₪ 0
זיכרון נייד מוצפן (דיסק און קי) -Apricorn | ASK3-240GB | 240GB | Aegis Secure Key | USB3.1 Encrypted Flash Key
1 × ₪ 0 -
×
 כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-1T | UltraLock | 1TB USB-C | M.2 NVMe | Write Protected
1 × ₪ 0
כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-1T | UltraLock | 1TB USB-C | M.2 NVMe | Write Protected
1 × ₪ 0
סכום ביניים: ₪ 0

 זיכרון נייד מוצפן (דיסק און קי) - Apricorn | ASK3-NXC-128GB | Aegis Secure Key | 3NXC | 128GB | USB 3.2 Type-C Encrypted Flash Key
זיכרון נייד מוצפן (דיסק און קי) - Apricorn | ASK3-NXC-128GB | Aegis Secure Key | 3NXC | 128GB | USB 3.2 Type-C Encrypted Flash Key  כונן קשיח חיצוני מוגן כתיבה - Kanguru | U3-2HDWP-4T | UltraLock | 4TB HDD | USB 3.0 | Write Protected
כונן קשיח חיצוני מוגן כתיבה - Kanguru | U3-2HDWP-4T | UltraLock | 4TB HDD | USB 3.0 | Write Protected  דיסק קשיח חיצוני חומרה מוצפנת - Apricorn | AFL3-2TB | Aegis Fortress L3 | 2TB HDD USB3.0 Hardware Encrypted
דיסק קשיח חיצוני חומרה מוצפנת - Apricorn | AFL3-2TB | Aegis Fortress L3 | 2TB HDD USB3.0 Hardware Encrypted  זיכרון נייד מוגן כתיבה מהירות גבוהה (דיסק און קי) - Kanguru KF3WP-512GB | SS3 | 512GB | USB 3.0 Write Protected
זיכרון נייד מוגן כתיבה מהירות גבוהה (דיסק און קי) - Kanguru KF3WP-512GB | SS3 | 512GB | USB 3.0 Write Protected  כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-2T | UltraLock | 2TB USB-C | M.2 NVMe | Write Protected
כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-2T | UltraLock | 2TB USB-C | M.2 NVMe | Write Protected  זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDF3000-64G | Defender 3000 | 64GB | USB 3.0 | FIPS 140-2 Level 3
זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDF3000-64G | Defender 3000 | 64GB | USB 3.0 | FIPS 140-2 Level 3  כונן חיצוני SSD מוצפן - Apricorn | ASSD-3PL256-480F | Aegis Padlock SSD | 480GB | USB3.0 | AES 256-Bit Hardware Encryption
כונן חיצוני SSD מוצפן - Apricorn | ASSD-3PL256-480F | Aegis Padlock SSD | 480GB | USB3.0 | AES 256-Bit Hardware Encryption  כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-500G | UltraLock | 500GB USB-C | M.2 NVMe | Write Protected
כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-500G | UltraLock | 500GB USB-C | M.2 NVMe | Write Protected  זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDF3000-256G | Defender 3000 | 256GB | USB 3.0 | FIPS 140-2 Level 3
זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDF3000-256G | Defender 3000 | 256GB | USB 3.0 | FIPS 140-2 Level 3  זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDFE30-16GB | Defender Elite 30 | 16GB | USB 3.0 | AES 256-Bit Hardware Encryption
זיכרון נייד מוצפן (דיסק און קי) - Kanguru | KDFE30-16GB | Defender Elite 30 | 16GB | USB 3.0 | AES 256-Bit Hardware Encryption  זיכרון נייד מוצפן (דיסק און קי) -Apricorn | ASK3-240GB | 240GB | Aegis Secure Key | USB3.1 Encrypted Flash Key
זיכרון נייד מוצפן (דיסק און קי) -Apricorn | ASK3-240GB | 240GB | Aegis Secure Key | USB3.1 Encrypted Flash Key  כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-1T | UltraLock | 1TB USB-C | M.2 NVMe | Write Protected
כונן חיצוני מוגן כתיבה - Kanguru | U3-NVMWP-1T | UltraLock | 1TB USB-C | M.2 NVMe | Write Protected